| In order to strengthen the risk management of information security, to establish information security promotion group, to establish information security risk management framework, formulated information security risk management framework, and regularly review the information security policy to ensure information security. |
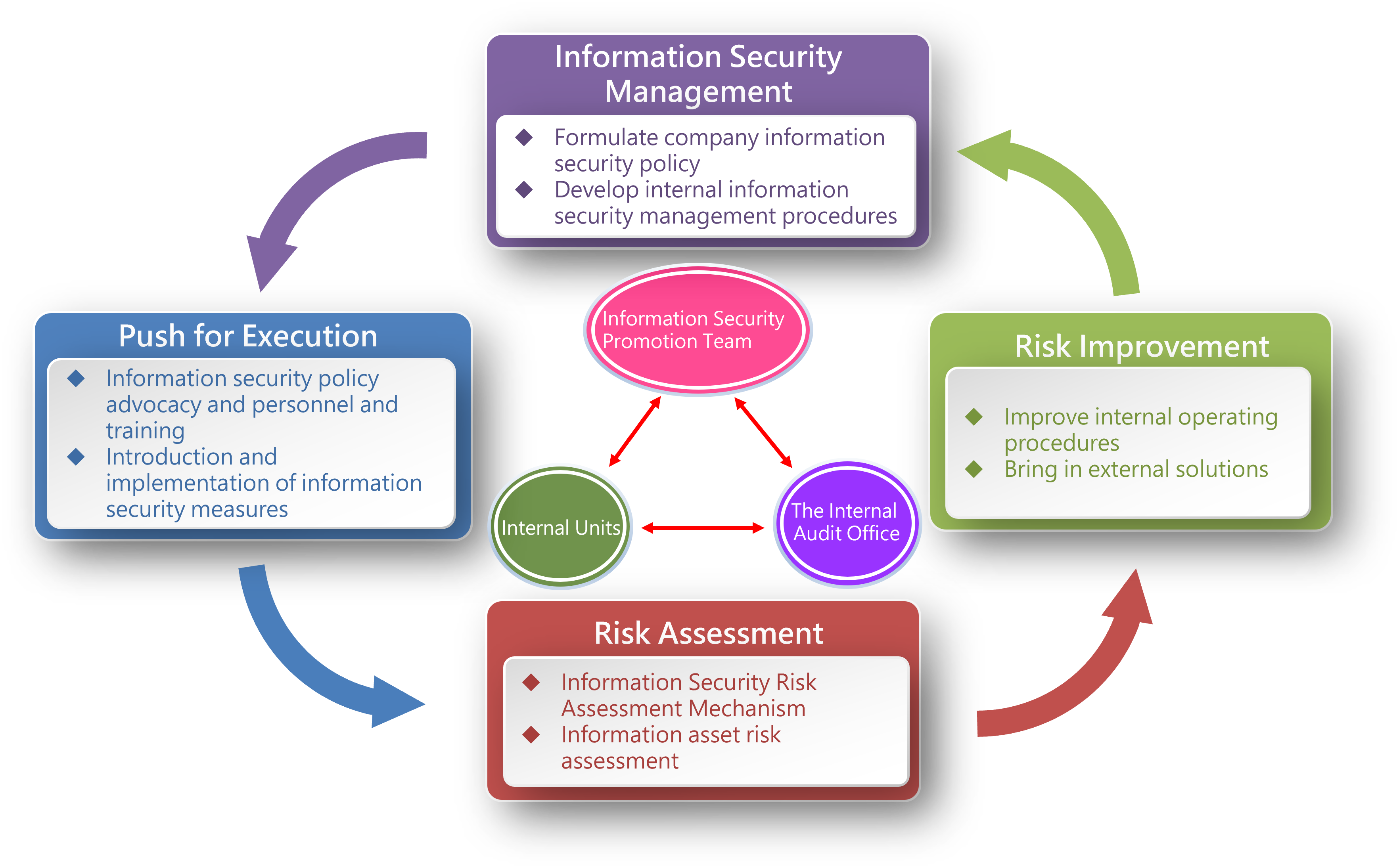
| Information security risk management framework: | |
|
|
|
|
|
|
|
|
|
|
|
|
| Information security policy and goals: |
| Purpose: | ||
| In order to protect the information and communication assets related to all computer systems of the company, including the physical environment, software and hardware facilities, network, data, information, etc., from the risks of leakage, destruction or loss due to internal or external threats, This policy is specially formulated. | ||
| Information security goals: | ||
| Ensure the correctness, usability, completeness and confidentiality of the company's information operations. Avoid the threat of internal and external information security incidents. In the event of an accident, it can respond quickly and resume normal operation in the shortest possible time to reduce the damage caused by the accident. | ||
| Information security management measures: | ||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
| Specific management plan: | ||
| Server equipment security management | Network Security Management | Virus Protection and Management | ||||||
|
|
|
||||||
| System Access Control | System Operation Sustainable | Education Training and Advocacy | ||||||
|
|
|
| Resources invested in information security management: |
|
||
|
||
|
||
|
||
|
||
|
||
|
||
| Propaganda by E-mail: | ||
| In 2024, a total of 12 information security promotion emails were sent. | ||
| Education Training: |
| Course Title | Trained proportion | |||
|
Mobile Device Security Threats and Protection |
12.1% |